Guide: Cloudflare SEO issues and how to protect yourself
TL;DR (Too long; didn’t read)
- You get what you pay for – invest in good DDOS protection
- If your rankings drop, don’t throw the baby out with the bath water – things are fixable
- CloudFlare can improve your rankings (with advanced configurations)
- CloudFlare is not responsible for your ranking drops – YOU ARE!
- If your rankings drop once on CloudFlare, get yourself on their private IPs
Introduction
Back on a Saturday morning in late June, I received an urgent phone call from a client whose digital marketing and technical SEO campaign have been run by us from the start. He was desperate for help, as both his developers and his hosting company could not assist him anymore. The developers could not get access to the servers, and the hosting company were refusing to route any external network calls to the client’s servers. Why? Because they were being DDOSed, and despite the hosting company having DDOS protection, they could not handle such an attack.
As soon as I heard the client’s account of what was happening, I knew this was not your average DDOS, and it was instead a well-planned operation. We had to do something to reduce damage, fast, as every single minute of down time meant there was a large sum of revenue being lost for the client.
When working with clients who are startups, they do not have hundreds of thousands of pounds to spend on advanced DDOS protection, and to be honest, there is no point in doing so when there are many other companies who offer such protection for a fraction of the price.
We had to make a quick decision about how we could protect the client’s SEO rankings – worth well over £500,000 a month in PPC – and at the same time protect them from DDOS attacks. Based on previous experience, we decided to put our client behind CloudFlare, and have their original IPs changed.
In less than a few hours, our client was back online; this time being protected by CloudFlare, using the Business plan. The threat graphs were phenomenal – I wish I had taken a screenshot at the time to show you guys. Since then, those threats have dropped to pretty much nothing, and a fraction of what they were, but we do still continue to see some threats on CloudFlare’s control panel.
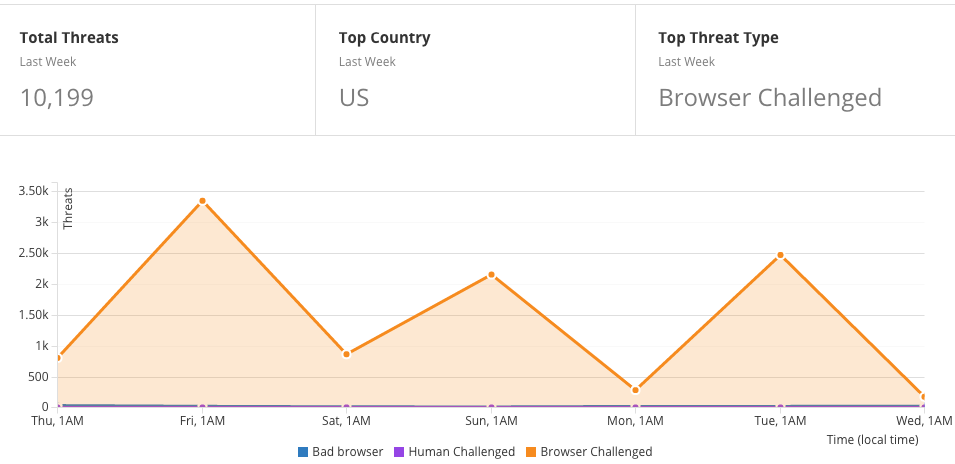
SEO Issues and Drop in Rankings
Sadly, in the SEO community CloudFlare tends to be feared, and the majority of agencies and companies avoid using it at any cost due to the possible impact it could have on SEO. This is because of bad press, and people thinking that their client’s rankings are going to drop and face problems post CloudFlare. In reality, and in the majority of cases, rankings do not drop. Since early this year we have moved more than half a dozen of our smaller clients behind CloudFlare. So far, in all cases we have seen small improvements but nothing significant, and in no cases had we seen any significant drops in rankings, until now.
A few days after moving the aforementioned case study client to CloudFlare, we faced two things: one good and one bad. On the positive side of things, the client was being protected from the DDOS and threats, and so the client was happy – that is, until we started seeing what every SEO agency or consultant fears; a drop in rankings of the high traffic keywords, especially those in the top 3. This was bad. So bad that the graph below can explain it much better than words could:
More than a third of the client’s main keyword rankings dropped off the top 3 spots. Even worse was that they completely stopped ranking, or dropped down to the second or third page. This was not just the rankings in one country – it happened globally.
Previous to this, we had never seen such a drop in rankings when moving clients behind CloudFlare, so we had to investigate what caused this issue, and come up with a solution promptly. At this point, out of many possible plans out action, there were two that stood out to us:
- To abandon CloudFlare and face DDOS attacks again
- To stay on CloudFlare and remain protected from DDOS attacks whilst we investigate further
The latter choice was the obvious one for us, as neither us nor the client were willing to face the same DDOS attacks again. Lucky for us, July and August is the client’s quiet time of the year, so we therefore had more time to fully investigate the issue.
Before I continue further about how we fixed the issue, here is a summary of how CloudFlare works for those of you who aren’t familar with it:
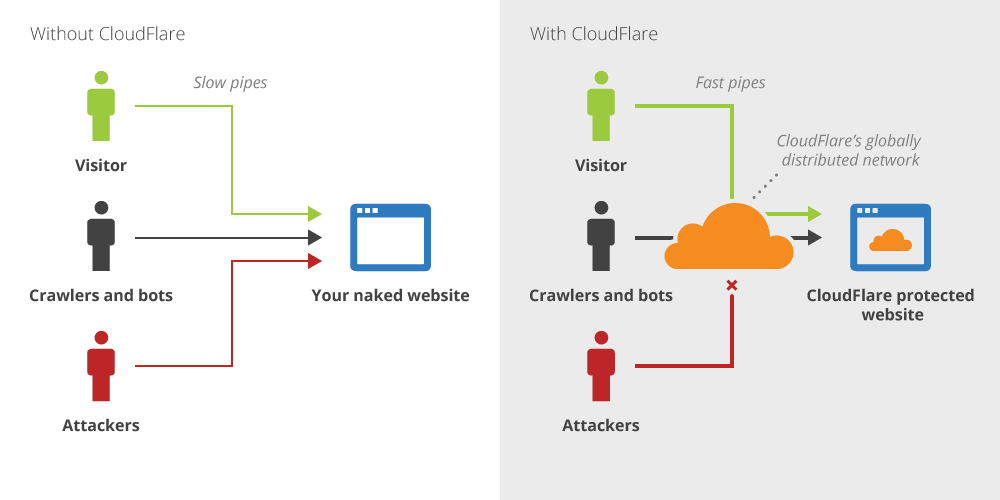
In a nutshell, CloudFlare is essentially an advanced proxy in front of a website, and all traffic passes through their network first – hence your servers are protected from attacks, if you need protection (this is as long as your server IP addresses are not know to the attackers, of course). At the same time, CloudFlare can cache your content, and optimise them in order to reduce server load and load time on the user side, due to their globally distributed network. The image below is CloudFlare’s own explanation of itself.
Fixing the SEO problems
Following our investigations – including comparisons to our other clients’ websites which were behind CloudFlare, but who had no rank drop – we discovered that this client was sadly sharing their IP addresses with some potentially questionable websites which, although they did not seem to have a bad SEO history or spammy content, did not look very legitimate either.
Over the next couple of weeks we had conversations with CloudFlare and the client to come up with a solution, and CloudFlare made us aware that the client can get private IP addresses (2, rather than the usual 5 shared) if we upload custom SSL certificates – a feauture that is not widely advertised.
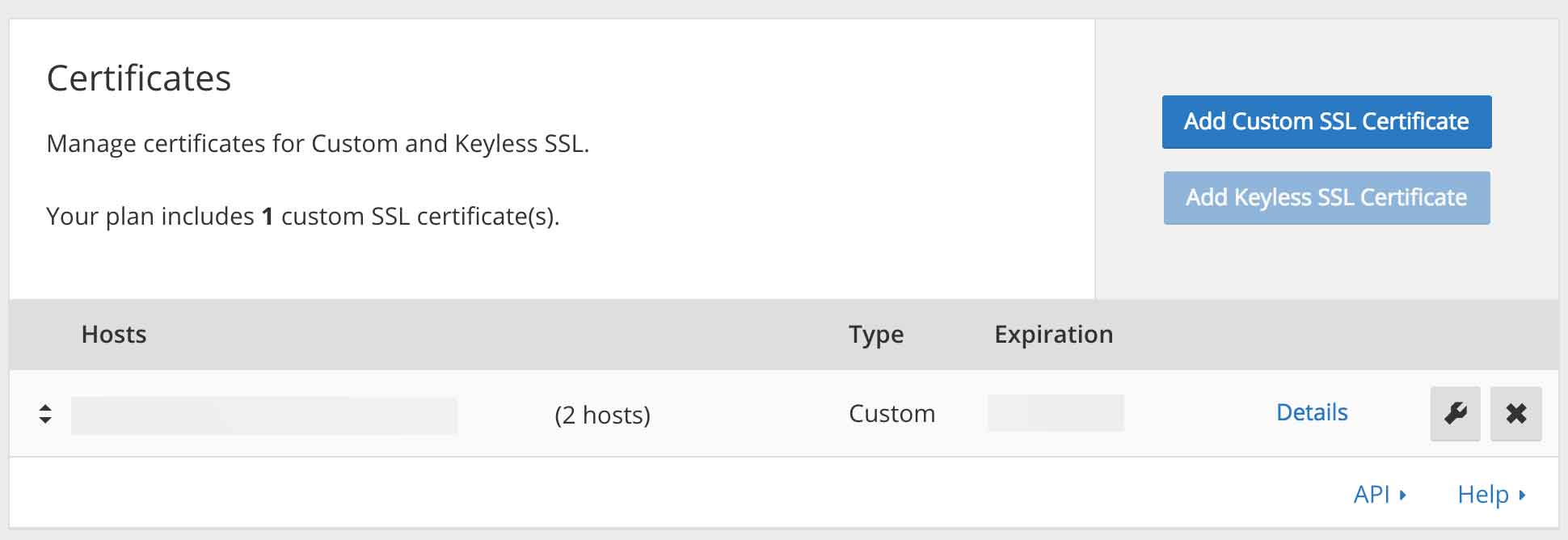
Following the purchase of a new SSL certificate, all we had to do was save it on CloudFlare’s control panel and then… wait. Within minutes of the upload our virtual private servers across the globe started reporting the new IP addresses, and to our relief they were private IP addresses, and not shared with any other domain – as expected.
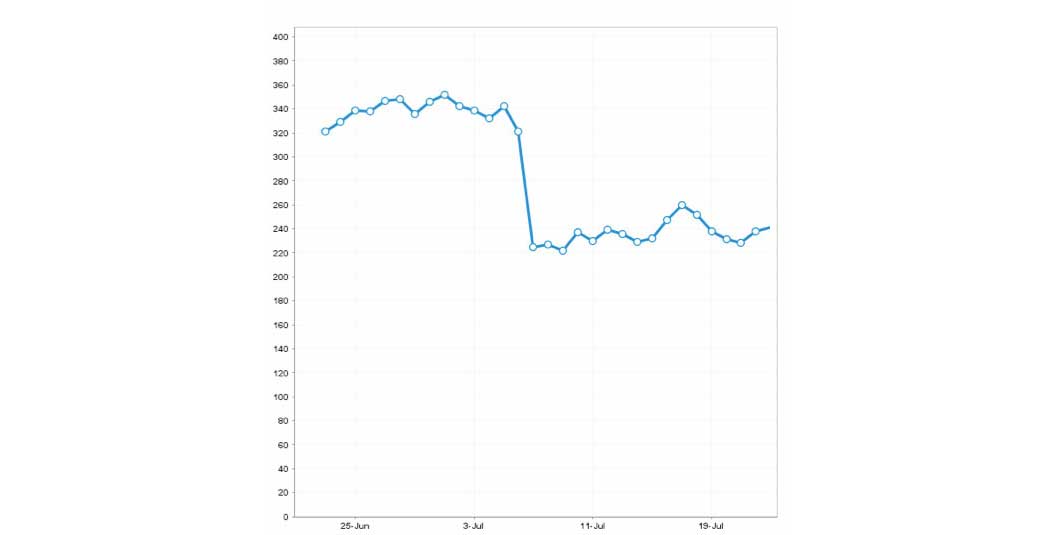
A couple of days later, we detected an unusual increase in pages being crawled by Google on our client’s website. For us this was a good sign, as it seemed like Google had taken notice of the change and, as expected, our rankings jumped back up to the original places, followed by increases globally.
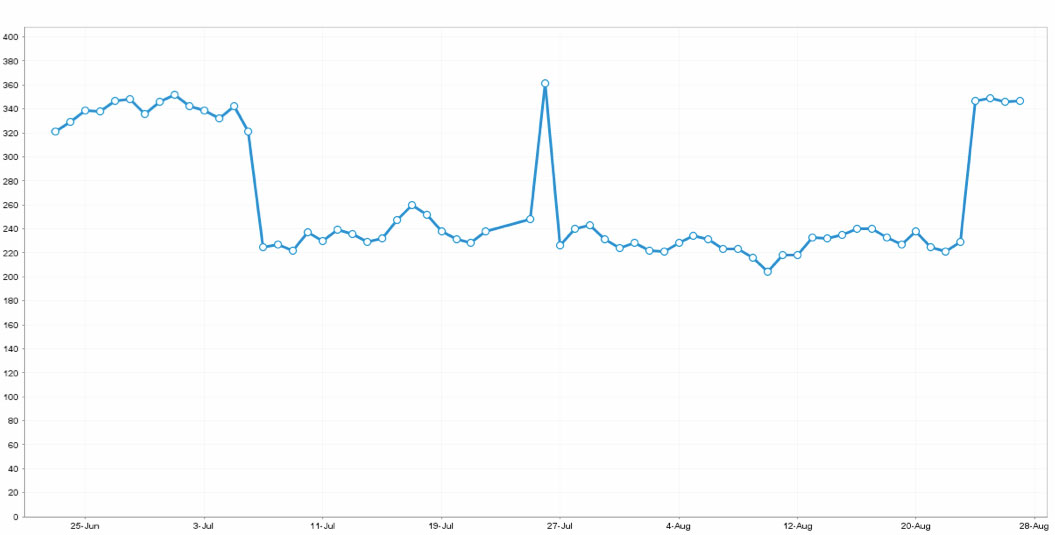
The graph above shows the number of non-branded keywords that ranked in the top 3 spots for our client before going on CloudFlare in late June, then the drops in early July, followed by the rankings going back up to the original state in August. Some of you may ask what actually happened in late July. We believe that occurrence was due to the Panda update rolling out at that time.
Conclusion
As we mentioned before, drops in rankings when going behind CloudFlare rarely happen, unless you end up sharing an IP with a network of websites that could potentially get that IP demoted within Google. Even then there is a solution, which is to come off those IP addresses, and potentially move to your own private IP address. If you want to ensure you are on a private IP before making the switch to CloudFlare, I recommend that you get your custom certificate saved before flipping the domain name servers – then you are guaranteed that you will not be sharing an IP address that could potentially damage your rankings.
I hope this case study helps others make their decisions based on facts and not rumours. As we specialise in technical SEO, we love CloudFlare and highly recommend them. We enjoy seeing how hard they work on improving their systems.
Please leave your comments below, and if you have questions or need any further advice, please do not hesitate to contact us and we will be more than happy to answer your questions.